SMTPDIAG is a tool supplied by Microsoft to test SMTP and DNS related issues in Exchange server.
Download SMTPDIAG
Download SMTPDIAG
Usage:
C:\SmtpDiag>SmtpDiag.exe tariq@microsoft.com tariq@cisco.com /v
You can also specify an external DNS with –d switch
Report:
What to look:
White text indicates action being taken.
Gray indicates informational results.
Green indicates a successful test result.
Red indicates a failed test result.
C:\SmtpDiag>SmtpDiag.exe tariq@microsoft.com tariq@cisco.com /v
You can also specify an external DNS with –d switch
Report:
What to look:
White text indicates action being taken.
Gray indicates informational results.
Green indicates a successful test result.
Red indicates a failed test result.
Successful mail flow:

Complete Output SMTPDIAG:
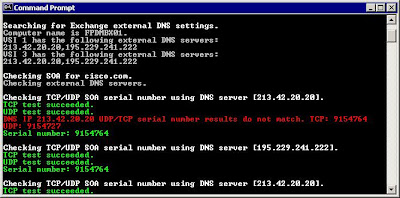
Searching for Exchange external DNS settings.
Computer name is FPDMBX01.
VSI 1 has the following external DNS servers:
213.42.20.20,195.229.241.222
VSI 3 has the following external DNS servers:
213.42.20.20,195.229.241.222
Checking SOA for cisco.com.
Checking external DNS servers.
Checking TCP/UDP SOA serial number using DNS server [213.42.20.20].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [195.229.241.222].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [213.42.20.20].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [195.229.241.222].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking internal DNS servers.
Checking TCP/UDP SOA serial number using DNS server [192.168.100.150].
TCP test succeeded.
UDP test failed.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [192.168.100.110].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
SOA serial number match: Passed.
Checking local domain records.
Starting TCP and UDP DNS queries for the local domain. This test will try to
validate that DNS is set up correctly for inbound mail. This test can fail for
3 reasons.
1) Local domain is not set up in DNS. Inbound mail cannot be routed to
local mailboxes.
2) Firewall blocks TCP/UDP DNS queries. This will not affect inbound mail,
but will affect outbound mail.
3) Internal DNS is unaware of external DNS settings. This is a valid
configuration for certain topologies.
Checking MX records using TCP: microsoft.com.
MX: mail.global.frontbridge.com (10)
Checking MX records using UDP: microsoft.com.
MX: mail.global.frontbridge.com (10)
A: mail.global.frontbridge.com [216.32.181.22]
Both TCP and UDP queries succeeded. Local DNS test passed.
Checking remote domain records.
Starting TCP and UDP DNS queries for the remote domain. This test will try to
validate that DNS is set up correctly for outbound mail. This test can fail for
3 reasons.
1) Firewall blocks TCP/UDP queries which will block outbound mail. Windows
2000/NT Server requires TCP DNS queries. Windows Server 2003 will use UDP
queries first, then fall back to TCP queries.
2) Internal DNS does not know how to query external domains. You must
either use an external DNS server or configure DNS server to query external
domains.
3) Remote domain does not exist. Failure is expected.
Checking MX records using TCP: cisco.com.
MX: rtp-mx-01.cisco.com (15)
MX: ams-inbound-a.cisco.com (20)
MX: syd-inbound-a.cisco.com (25)
MX: sj-inbound-a.cisco.com (10)
MX: sj-inbound-b.cisco.com (10)
MX: sj-inbound-c.cisco.com (10)
MX: sj-inbound-d.cisco.com (10)
MX: sj-inbound-e.cisco.com (10)
MX: sj-inbound-f.cisco.com (10)
A: sj-inbound-a.cisco.com [128.107.234.204]
A: sj-inbound-b.cisco.com [128.107.234.205]
A: sj-inbound-c.cisco.com [128.107.234.206]
A: sj-inbound-d.cisco.com [128.107.243.13]
A: sj-inbound-e.cisco.com [128.107.243.14]
A: sj-inbound-f.cisco.com [128.107.234.207]
A: rtp-mx-01.cisco.com [64.102.255.47]
A: ams-inbound-a.cisco.com [64.103.36.153]
A: syd-inbound-a.cisco.com [64.104.252.248]
Checking MX records using UDP: cisco.com.
MX: rtp-mx-01.cisco.com (15)
MX: ams-inbound-a.cisco.com (20)
MX: syd-inbound-a.cisco.com (25)
MX: sj-inbound-a.cisco.com (10)
MX: sj-inbound-b.cisco.com (10)
MX: sj-inbound-c.cisco.com (10)
MX: sj-inbound-d.cisco.com (10)
MX: sj-inbound-e.cisco.com (10)
MX: sj-inbound-f.cisco.com (10)
Both TCP and UDP queries succeeded. Remote DNS test passed.
Checking MX servers listed for tariq@cisco.com.
Connecting to sj-inbound-f.cisco.com [128.107.234.207] on port 25.
Received:
220 sj-inbound-f.cisco.com ESMTP
Sent:
ehlo microsoft.com
Received:
250-sj-inbound-f.cisco.com
250-8BITMIME
250-SIZE 33554432
250 STARTTLS
Sent:
mail from:
Received:
250 senderok
Sent:
rcpt to:
Received:
250 recipientok
Sent:
quit
Received:
221 sj-inbound-f.cisco.com
Successfully connected to sj-inbound-f.cisco.com.
Connecting to sj-inbound-e.cisco.com [128.107.243.14] on port 25.
Received:
220 sj-inbound-e.cisco.com ESMTP
Sent:
ehlo microsoft.com
Received:
250-sj-inbound-e.cisco.com
250-8BITMIME
250-SIZE 33554432
250 STARTTLS
Sent:
mail from:
Received:
250 senderok

Complete Output SMTPDIAG:
Searching for Exchange external DNS settings.
Computer name is FPDMBX01.
VSI 1 has the following external DNS servers:
213.42.20.20,195.229.241.222
VSI 3 has the following external DNS servers:
213.42.20.20,195.229.241.222
Checking SOA for cisco.com.
Checking external DNS servers.
Checking TCP/UDP SOA serial number using DNS server [213.42.20.20].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [195.229.241.222].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [213.42.20.20].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [195.229.241.222].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
Checking internal DNS servers.
Checking TCP/UDP SOA serial number using DNS server [192.168.100.150].
TCP test succeeded.
UDP test failed.
Serial number: 9154727
Checking TCP/UDP SOA serial number using DNS server [192.168.100.110].
TCP test succeeded.
UDP test succeeded.
Serial number: 9154727
SOA serial number match: Passed.
Checking local domain records.
Starting TCP and UDP DNS queries for the local domain. This test will try to
validate that DNS is set up correctly for inbound mail. This test can fail for
3 reasons.
1) Local domain is not set up in DNS. Inbound mail cannot be routed to
local mailboxes.
2) Firewall blocks TCP/UDP DNS queries. This will not affect inbound mail,
but will affect outbound mail.
3) Internal DNS is unaware of external DNS settings. This is a valid
configuration for certain topologies.
Checking MX records using TCP: microsoft.com.
MX: mail.global.frontbridge.com (10)
Checking MX records using UDP: microsoft.com.
MX: mail.global.frontbridge.com (10)
A: mail.global.frontbridge.com [216.32.181.22]
Both TCP and UDP queries succeeded. Local DNS test passed.
Checking remote domain records.
Starting TCP and UDP DNS queries for the remote domain. This test will try to
validate that DNS is set up correctly for outbound mail. This test can fail for
3 reasons.
1) Firewall blocks TCP/UDP queries which will block outbound mail. Windows
2000/NT Server requires TCP DNS queries. Windows Server 2003 will use UDP
queries first, then fall back to TCP queries.
2) Internal DNS does not know how to query external domains. You must
either use an external DNS server or configure DNS server to query external
domains.
3) Remote domain does not exist. Failure is expected.
Checking MX records using TCP: cisco.com.
MX: rtp-mx-01.cisco.com (15)
MX: ams-inbound-a.cisco.com (20)
MX: syd-inbound-a.cisco.com (25)
MX: sj-inbound-a.cisco.com (10)
MX: sj-inbound-b.cisco.com (10)
MX: sj-inbound-c.cisco.com (10)
MX: sj-inbound-d.cisco.com (10)
MX: sj-inbound-e.cisco.com (10)
MX: sj-inbound-f.cisco.com (10)
A: sj-inbound-a.cisco.com [128.107.234.204]
A: sj-inbound-b.cisco.com [128.107.234.205]
A: sj-inbound-c.cisco.com [128.107.234.206]
A: sj-inbound-d.cisco.com [128.107.243.13]
A: sj-inbound-e.cisco.com [128.107.243.14]
A: sj-inbound-f.cisco.com [128.107.234.207]
A: rtp-mx-01.cisco.com [64.102.255.47]
A: ams-inbound-a.cisco.com [64.103.36.153]
A: syd-inbound-a.cisco.com [64.104.252.248]
Checking MX records using UDP: cisco.com.
MX: rtp-mx-01.cisco.com (15)
MX: ams-inbound-a.cisco.com (20)
MX: syd-inbound-a.cisco.com (25)
MX: sj-inbound-a.cisco.com (10)
MX: sj-inbound-b.cisco.com (10)
MX: sj-inbound-c.cisco.com (10)
MX: sj-inbound-d.cisco.com (10)
MX: sj-inbound-e.cisco.com (10)
MX: sj-inbound-f.cisco.com (10)
Both TCP and UDP queries succeeded. Remote DNS test passed.
Checking MX servers listed for tariq@cisco.com.
Connecting to sj-inbound-f.cisco.com [128.107.234.207] on port 25.
Received:
220 sj-inbound-f.cisco.com ESMTP
Sent:
ehlo microsoft.com
Received:
250-sj-inbound-f.cisco.com
250-8BITMIME
250-SIZE 33554432
250 STARTTLS
Sent:
mail from:
Received:
250 sender
Sent:
rcpt to:
Received:
250 recipient
Sent:
quit
Received:
221 sj-inbound-f.cisco.com
Successfully connected to sj-inbound-f.cisco.com.
Connecting to sj-inbound-e.cisco.com [128.107.243.14] on port 25.
Received:
220 sj-inbound-e.cisco.com ESMTP
Sent:
ehlo microsoft.com
Received:
250-sj-inbound-e.cisco.com
250-8BITMIME
250-SIZE 33554432
250 STARTTLS
Sent:
mail from:
Received:
250 sender